ISMS & ISO 27001
Information Security Management System
Stay secure with a structured ISO 27001 framework
Gain a clear overview and actionable plan to establish a structured approach to managing your information security.
Tired of relying on spreadsheets and fragmented systems?
Spreadsheets and project management tools aren’t built for managing information security. RISMA is purpose-built for ISMS management, providing a robust, sustainable security framework aligned with ISO 27001 best practices—without the complexity.
Gain total visibility
With a glance, you’ll have a total overview through a complete mapping of your information assets allowing you to easily identify and close gaps.
Complete visual mapping of all your information assets
Manage policies and proceduresin the process library
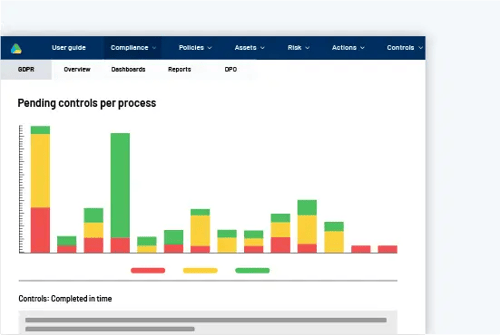
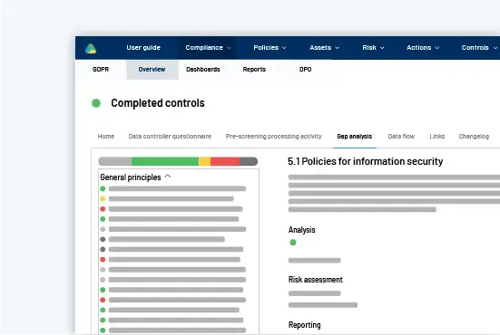
Tailored action plan
Turn your insights and gaps into a tailored and comprehensible action plan with follow-up actions and controls to ensure things get done and on time.
Create transparency across the different departments
Create annual wheels with automatic controls
Help employees save time and resources
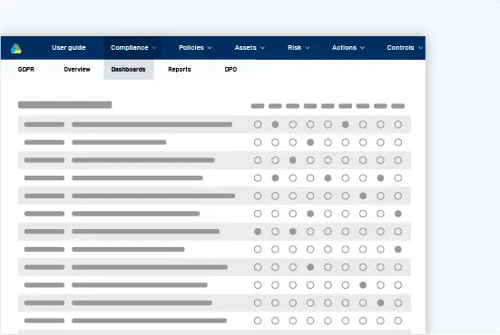
Continuous compliance
With on-going controls, you can make sure gaps remain closed. It ensures your continuous compliance and supports the 114 Annex A control objectives in ISO27001.
Automation ensures tasks are completed correctly & ontime
Central catalog of IT Controls
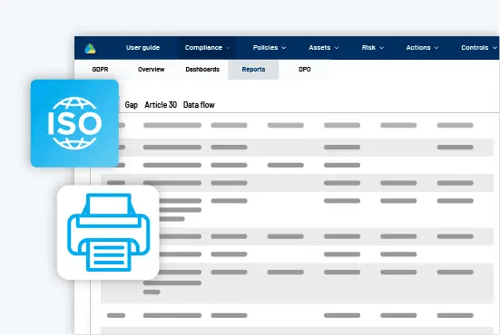
Report & documentation
Easily extract a complete Statement of Applicability (SoA) document, report on progress, and get a full documentation of the organization's security.
Risk documentation report
Report progress on the action plans
Key features in our ISMS solution
ISO 27701 - Combined ISMS and GDPR solution
Information security plays an important role in the EU’s General Data Protection Regulation, which aims to ensure that all companies increase information security, create transparency, and secure data subjects’ rights when it comes to big data flows inside an organization. By combining our ISMS solution with our GDPR solution, you and your colleagues can work towards complying with the data protection regulation and following the ISO 27701 standard at the same time.
General Data Protection Regulation
Risk Management
ISO 27001 compliance
-
Step 1Risk assessment
-
Identify the risks of your organization and gain an overview of where efforts should be focused.
The risk assessments are based on our threat and vulnerability catalogs as well as probability, allowing you to target efforts towards the areas that exceed your risk appetite. Then, you can do an impact assessment - FIT, CIA, or your own setup.
-
Step 2Identify information assets
-
Identify information assets that are relevant to your information security – i.e. data controllers, data processors, suppliers, and systems.
It will provide an overview of the scope of your information security work. This means you get a strategic management tool that helps you determine the objectives, boundaries, and responsibilities of your IT security policy.
-
Step 3Gather information
-
Using a structured questionnaire, based on the control objectives of the ISO 27001 standard, you are guided through the information gathering process.
The ISMS solution makes it possible to delegate information tasks to different people, allowing the most qualified employees to provide the input. You can also create specific questionnaires that target your data processors and system administrators.
-
Step 4Gap analysis
-
Once the necessary information has been collected, you need to create and associate risks with your systems and data processors. This will allow you to make a gap analysis where you compare the 114 Annex A control objectives with your information.
Along the way, you can easily extract a complete Statement of Applicability (SoA) document and get a full documentation of the organization's security measures.
-
Step 5Mitigating actions and controls
-
Once the gap analysis has been made, you will have a 114-step plan for your further work. Link controls or initiatives at each step that minimize the gap and mitigate the identified risk. Controls may include, for example, samples, logs, and back up tests.
Implementation of ISO 27001 solution
Our ISO 27001 ISMS software has an intuitive user interface, making it easy to work with. However, the implementation process can be a big task to handle on your own.
To get the best possible start with RISMA's ISMS software, our colleagues in Customer Success are ready to help you get started on a planned implementation process. They will also continuously support you so that you get the most value out of your solution.

A GRC platform to bring the organization together
Power your organisation by connecting data, teams, action and reporting in an integrated GRC platform. Whether you deploy one, two, or all our solutions, RISMA GRC platform provides great value by boosting collaboration, increasing visibility, and saving time for everyone involved.
-
Internal audit streamlined
-
Effortlessly automate, document and report all your controls - including assessment, mitigation and monitoring in one simple platform.
-
Risk management organized
-
Define, assess, analyze and mitigate your organization’s risks and turn your insight into strategic assets.
-
GDPR Compliance Unified
-
Manage compliance frameworks, controls, risks, policies, and reporting in one integrated solution.
FAQ
What is ISO / IEC 27701?
It is called ”Security techniques — Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management - Requirements and guidelines".
According to Dansk Standard, it is a management tool that provides knowledge of workflows and measurement that organizations should establish to achieve adequate protection of personal data.
It is an extension of ISO 27001 for information security. Thus, it extends the standard with special requirements for the processing of personal data.
What are the benefits of obtaining ISO/IEC 27001/2 certification for my organization?
ISO/IEC 27001/2 certification is not a legal requirement, but many organizations choose to implement the standard in order to benefit from ISO's best practices and gain a competitive advantage.
Certification provides a robust framework for effective information security management, enabling organizations to proactively mitigate the risk of cyber attacks and limit the impact of data breaches, thus ensuring business continuity. '
Some of the benefits of obtaining ISO/IEC 27001/2 certification include:
- Improved trust and confidence from stakeholders
- Increased customer satisfaction and loyalty
- Enhanced reputation and credibility
- Improved risk management and decision making
- Greater efficiency and productivity in managing information security
- Compliance with legal and regulatory requirements.
What is the Statement of Applicability (SoA) in ISO 27001 documentation?
The Statement of Applicability (SoA) is a status report that outlines an organization's work on information security and is an integral component of the ISO 27001 standard. Essentially, it serves as a declaration of an organization's chosen level of information security in a given process, along with the rationale behind selecting respective measures. The SoA provides a valuable link between an organization's risk assessment and risk treatment.
The SoA is an indispensable tool in relation to information security, as it contains justifications for the inclusion or exclusion of specific security measures. As a result, an organization must evaluate all information security controls - including those that may not be applicable to a particular case - to ensure comprehensive and effective information security management. The SoA typically includes a list of security controls and their corresponding justifications for selection or exclusion.
The SoA can be a valuable tool for demonstrating compliance with external stakeholders, such as regulatory bodies or clients. It can also be used as a reference for ongoing security management, providing a clear overview of the security measures and their justifications. The SoA is an essential part of ISO 27001 certification, as it demonstrates that an organization has identified and implemented appropriate security measures to manage and mitigate its risks.
What is ISMS (Information Security Management System)?
ISMS is an abbreviation for Information Security Management System, which is a management system for managing the information security of organizations. With an effective ISMS, organizations can ensure business continuity by proactively mitigating the risk of cyber-attacks and limiting the impact of potential data breaches.
Implementing an appropriate level of information security requires a comprehensive understanding of the organization's departments and workflows. ISO 27001 can be used as a starting point for information security work. Although the standard does not directly specify specific security measures, it describes best practices for managing security both internally and externally through its 114 Annex A control objectives.
The goal is to protect three important aspects of information:
- Confidentiality - to ensure that information is not accessible or disclosed to unauthorized persons, devices, or processes.
- Integrity - to ensure that information is complete and accurate and protected against corruption.
- Availability - to ensure that information is accessible and usable by authorized users.


